Blog
ESP8266: Reflash Dance!
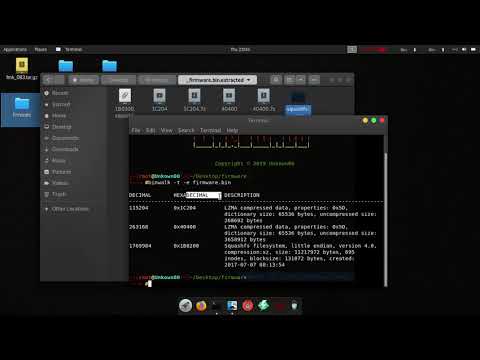
signature match. Additionally, parallel operation has not been thoroughly tested. This is a recursive firmware extractor that aims to extract a kernel image and/or compressed filesystem from a Linux-based firmware image.
Some cryptographic click Here algorithms make use of constant structures to define their initial state. By profiling the byte distribution of a file, it is possible to recognize different file encodings and even estimate the possible languages in which the text is written. A more mundane example of this could be given with our language. Taking as a symbol a word instead of a byte, if you analyze the entropy of a literary work, you will get an unknown entropy value X.
- We appreciate the network administrator’s assistance in pointing out the target file.
- The linker script is what describes the region where that data should go, and that it should be located in flash.
- In such cases the bootloader takes the location from documentation, and the real firmware
- When the command completes the device is not in programming mode anymore.
- In compliment to manually making changes, one can use pre-built IPKG
This could be done using the Payload Dumper Tool, either on a PC or on an Android device. The stock boot image is required not just for rooting and unrooting, but also for fixing boot loops. The Stock Boot Image file is a required component of the firmware file that contains a set of codes that must be executed on the device every time you switch it on. Therefore, it always comes with the stock firmware file from the manufacturer in a compressed file.
On Huawei/Honor Firmware, the Boot.img files are included within the update.app file. To obtain the stock Boot.img file for Huawei smartphones, extract the update.app file. In the terminal, the directions where the rising and falling edges of the entropy are located are shown, which can be useful to delimit the sections.
